Class 12 Computer Science Model Question Solutions
 |
| Class 12 Computer Science Model Question Solutions | Grade 12 Computer Science NEB Solutions |
In this collection, we have included Questions and solutions from computer science for class 12. The questions we have mentioned, have a high probability of being asked in your board exam.
 |
| Class 12 Computer Science Model Question Solutions |
Long Answer Questions
1. What is the Entry- Relationship Data Model? Give an ER diagram for a database showing fatherhood, motherhood, and spouse relationships among men and women.
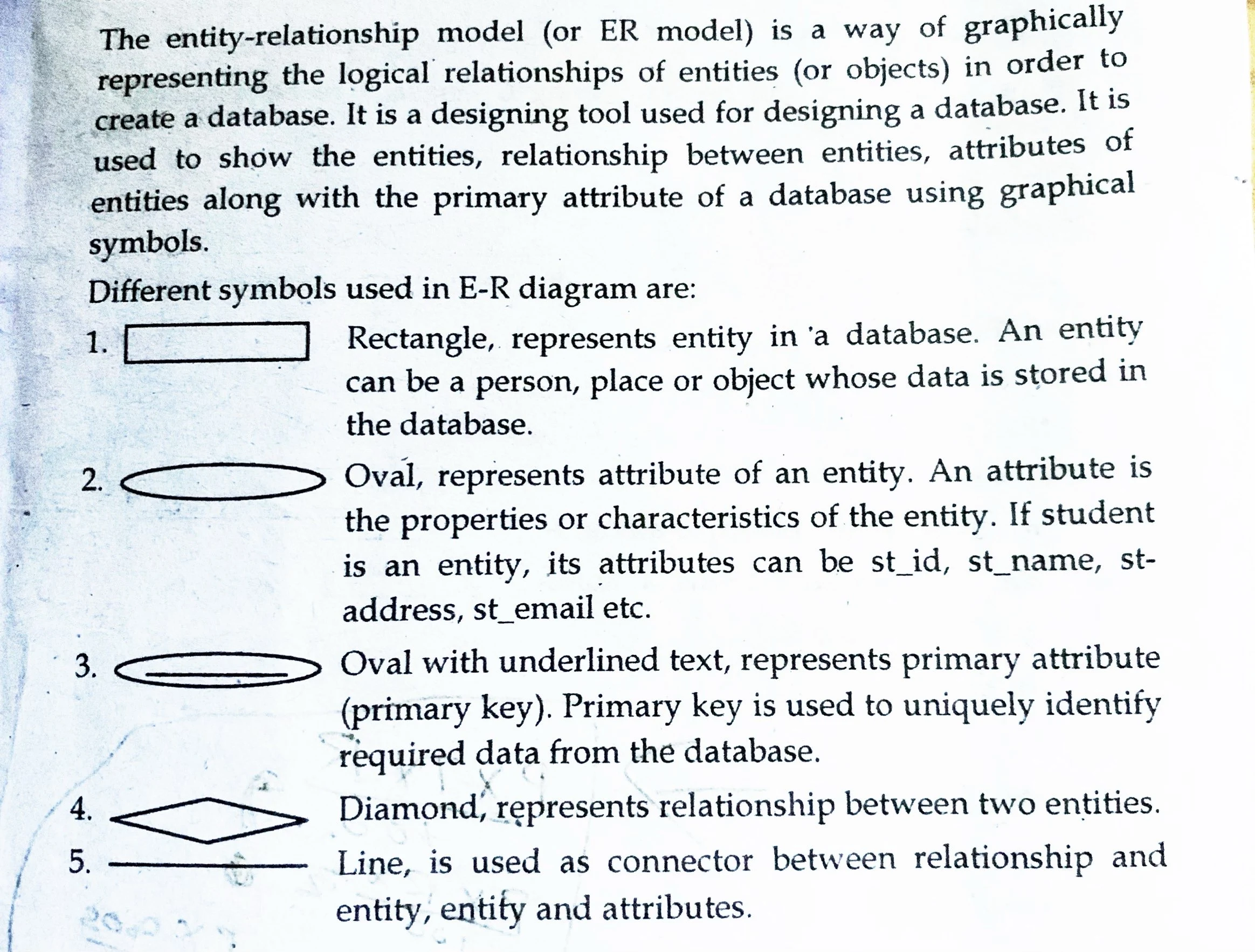 |
| Entry- Relationship Data Model |
 |
| Entry- Relationship Data Model |
2. The rate of interest offered by a bank on fixed deposit:
i. Period < 6 months 5 %
ii. Period 6 to 12 months 6%
iii. Above 1 year 10 %
Write a flowchart and program using C language to calculate the monthly interest of customers.
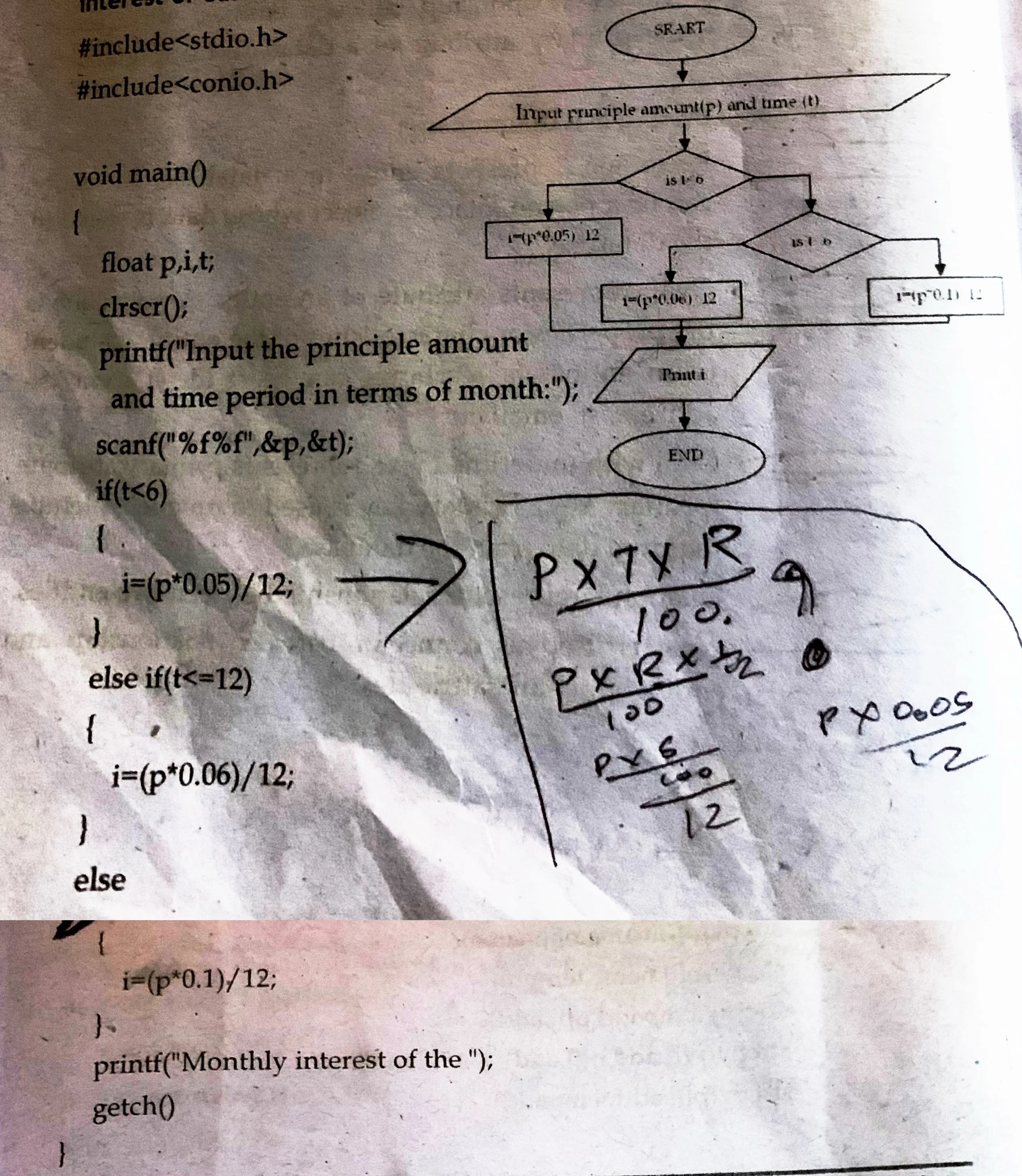 |
| Class 12 Computer Science Long Answer Questions |
3. Write a program that can read several different names and addresses in the computer, and rearrange the names into alphabetical order. Make use of structure variables.
 |
| Grade 12 Computer Science NEB Solutions |
4. Write a program that can read successive records from the new data file and display each record on the screen in an appropriately formatted form.
 |
| Class 12 Computer Science Model Question Solutions |
5. Write a program with a function and input menu from the keyboard and activate these functions.
 |
| Class 12 Computer Science Long Answer Questions |
Group B (Short Answer Questions)
6. What is a feasibility study? Why feasibility study is important in the system analysis phase? Explain.
Meaning of Feasible Study
A feasibility study is the process of analyzing whether the proposed system is feasible to develop or not. It is done to determine, if the system would be constructive, profitable, and meaningful for the organization or not. A feasibility study is conducted once the system goal is set. The feasibility study is basically the test of the proposed system in its workability, effective use of resources, and cost efficiency. Different levels of feasibility studies are technical feasibility, economical feasibility, behavioral feasibility, schedule feasibility, operational feasibility, legal feasibility, etc.
Necessity of Feasible Study Before Designing a System
Feasible study is necessary before designing a system because:
- It determines whether the proposed system meets the goal of the clients or not.
- It determines the strengths and limitations before starting to develop the system.
- It focuses on the boundary of the system's outline.
- It suggests new opportunities through the investigation process.
- It provides quality information for decision-making.
- It helps to increase investment in the system.
- It provides documentation of the investigated system.
- It allows new technologies and development areas for faster processing, more storage, and lower costs than ever before.
7. What are the different types of LAN topology? Write the merits and demerits of Star Topology. Different Types of LAN Topology
Network topology is the arrangement of computers connected in a network. It defines how the computers are connected with each other to form a network.
Different network topologies are:
- Bus topology
- Star topology
- Ring topology
- Mesh topology
- Tree topology
- Hybrid topology
Bus topology
In this topology, all the computers are connected to the central cable called a bus. It uses a bus and
terminators at both ends of the cable. It uses a broadcasting mechanism for the transmission of
data.
Star topology
In a star topology, each computer or node is connected to the central device such as a hub. Data on the star network passes through the hub before reaching its destination. Broadcasting also uses mechanisms for data transmission.
Ring topology
In the ring topology, each connected computer is
with nearby computers on a point-to-point basis so that the entire system is in the form of a ring. That is, the entire computers are connected in a closed loop. In this topology, data is transmitted in only one direction. Data is transmitted by passing a token from one computer to another.
Mesh Topology
Each computer is connected to all other computers in the network forming a mesh. It requires more cable for each and every connection. It is highly reliable.
Tree topology
The tree topology is a logical extension of the bus topology or star topology. It is mainly used to connect a large number of computers in the network.
Hybrid topology
Hybrid topology is the combination of two
more or topologies. Networks are widely designed by using this topology. Some of the commonly used hybrid topologies are star-bus topology, star-ring topology, and bus-ring topology. Hybrid topology is developed to take advantage of two or more topologies. It is also formed when different networks, developed at different times are connected.
Merits and Demerits of Star Topology
Merits
- It is easier to establish and manage.
- Troubleshooting is easier.
- Adding or removing computers is easier.
- Failure of a computer will not affect others.
Demerits
- It is more expensive than bus topology.
- Data traffic, collision rate, and error rate will be higher.
- Transmission speed will be slower.
- Failure of the hub will collapse the network.
8. Write short notes on (any two):
a. Coaxial cable
It is commonly used for broadband connection and cable TV networks. It is appropriate for connecting computers in a MAN (Metro-Politian Area Network). It can transmit data at a faster speed and for a longer distance than a twisted pair cable. It is expensive, heavier, thick, and difficult to bend compared to twisted pair cables. It consists of a single copper wire covered by a plastic layer and aluminum foil. It requires a BNC connector to connect the cable to the computer.
b. Fiber-Optic Cable
It is also called an Optical fiber cable. It is the fastest transmission medium at present. It is popularly used for long-distance communication and telecommunication networks. It transmits data in the form of light signal. It contains multiple small hair-like fibers made of glass or plastic. Data is transmitted through the fiber in the form of a light signal using total internal reflection of light. It requires an ST connector.
c. Switch
A switch is a networking device that connects multiple computing devices in a network. It receives data from a computer, amplifies it, and forwards it to the intended receiver. It doesn't broadcast data, so data traffic, collision rate, and error rate are low. However, it is expensive and requires technical knowledge to manage it.
9. Differentiate between array and structure with suitable examples.
 |
| Differentiate between array and structure |
10. What do you mean by parameters 'Passing by value' and 'Passing by reference' in C? Explain with a suitable example.
Passing by value (Call by value) is the process of calling the function with value as arguments. It passes the value of the variable during the function call.
Example:
#include<stdio.h>
#include<conio.h>
void increment(int);
void main()
{
int n=5;
clrscr();
printf("Value of n before function call=%d",n) increment(n);
printf("\nValue of n after function call=%d",n); getch()
}
void increment(int n)
{
n=n+5;
}
Output of the above program:
Value of n before function call=5
Value of n after function call=5
In the above program value of n is passed from main() to increment(). It only passes the copy of the value to increment(). The changes made on the n in increment() are effective only for the function increment() and not for other functions. So, main() will not display the updated value. Passing by reference (Call by reference) is the process of calling the function with memory address as arguments. It passes the memory address of the variable during the function call.
Example:
#include<stdio.h>
#include<conio.h>
void increment(int);
void main()
{
int n=5;
clrscr();
printf("Value of n before function call=%d",n)
increment(&n);
printf("\nValue of n after function call=%d",n); getch()
}
void increment(int *n)
{
*n=*n+5;
}
Output of the above program:
Value of n before function call=5
Value of n after function call=10
In the above program address of n is passed from main() to increment(). The changes made on the address of n in increment() are effective for all the functions. So, main() will display the updated value.
11. Explain the terms Polymorphism and inheritance.
Polymorphism
The word polymorphism is derived from the Latin words; i.e. 'poly' means 'many' and 'morphos' means 'forms'. Thus 'polymorphism' means 'having many forms'. Object-oriented programming languages try to make existing code easily modifiable without actually changing the code. Polymorphism means that the same functions may behave differently in different classes. Thus, "Polymorphism enables the same function to behave differently on different classes".
Inheritance
The idea of classes leads to the idea of inheritance. In our daily lives, we use the concept of classes being divided into subclasses. We know that a class of animals can be divided into mammals, amphibians, insects, and reptiles. A class of vehicles is divided into cars, trucks, buses, and motorcycles.
The principle in this sort of division is that each subclass shares common properties with the class from which it is derived. For example, all vehicles in a class may share similar properties of having wheels and a motor. Thus, "Inheritance is the property that allows the reuse of an existing class to build a new class".
12. Describe the limitations of using getchar() and putchar() functions for reading strings.
getchar returns only one character at a time from a standard input device. The getcha accepts all types of characters even space, tab, blank, and return. This function has a limitation, i.e. this isn't used for numeric operations and also not used for looping.
Example:
#include<stdio.h>
#include<conio.h>
void main()
{
char c;
c = getchar();
printf("\n Input character = %c", c);
getch ();
}
putchar transmits a single character to a standard output device. This function accepts all types of characters even space, tab, and blank. This function also has a limitation, which isn't used for numeric operations and is not displayed for loops.
Example:
#include<stdio.h>
#include<conio.h>
void main()
{
char ch;
printf("Enter any letter:-");
ch = getchar();
printf(" Output)");
putchar (ch);
getch();
}
13. What do you understand by AI? How it may affect society?
Meaning of Al
AI (Artificial Intelligence) is the ability of an artificial object through which it will have the ability to learn, think, reason, make decisions, or react like humans. AI has both positive effects and negative effects on the society.
Positive effects of Al
- Al has supported in the field of Medical diagnosis, automated controlling of industry/vehicle, analysis of stock market/business, robotics, etc.
- It has supported handicapped people in their daily activities.
- The use of computing devices has been easier.
- It has replaced humans in dangerous situations.
Negative effects of Al
- Al has made humans more dependent on machines.
- Computers are replacing humans thus, increasing the unemployment problem.
14. Write short notes on (any two):
a. Cyber Law
Cyber law deals with the legal issues of Internet usage and all devices connected over the network, and their proper use to prevent and control cyber crimes. It is a term that summarizes the legal issues related to the use of communicative, transactional, and distributive aspects of networked information devices and technologies. It addresses the legal issues related to intellectual property, privacy, and freedom of expression in computer ethics inside the nation or the whole world.
b. Normalization
Normalization is the process of breaking down a complex and large table or relation into smaller multiple tables. It is used to reduce the repetition of data, identify dependencies between the data, and make the database more flexible and easier to use.
The advantages of normalization are:
- It reduces data redundancy. It reduces wastage of storage.
- It removes inconsistency in the database. It simplifies the structure of tables.
- It makes the database operation easier.
- It avoids loss of data from the database.
- It improves the performance of the system.
Normalization uses different normal forms. Some of the normal forms are the first Normal Form (1NF), Second Normal Form (2NF), and Third Normal Form (3NF).